In today’s cyber landscape, the importance of robust security solutions cannot be overstated. The Juniper Enterprise Firewall is a powerful tool for organizations aiming to protect their networks. As cybersecurity expert Dr. Emily R. Lane states, "A strong firewall is the backbone of an effective security strategy." This statement encapsulates the essence of why enterprises are turning to the Juniper Enterprise Firewall to safeguard their digital environments.
The Juniper Enterprise Firewall offers advanced features such as threat intelligence and traffic monitoring. It allows businesses to respond swiftly to potential threats. However, leveraging its full potential requires a clear understanding of its functionalities. Some organizations struggle with configuration or fail to adapt to its continuous updates. These challenges highlight the need for ongoing education in the ever-evolving security field.
Deploying the Juniper Enterprise Firewall must also come with a commitment to regular review and adaptation. The digital world changes rapidly, and static defenses can become obsolete. Organizations must reflect on their security practices and ensure the Juniper Enterprise Firewall is aligned with their unique needs and threat landscapes. Embracing this critical security tool involves recognizing both its capabilities and the responsibilities that come with its use.
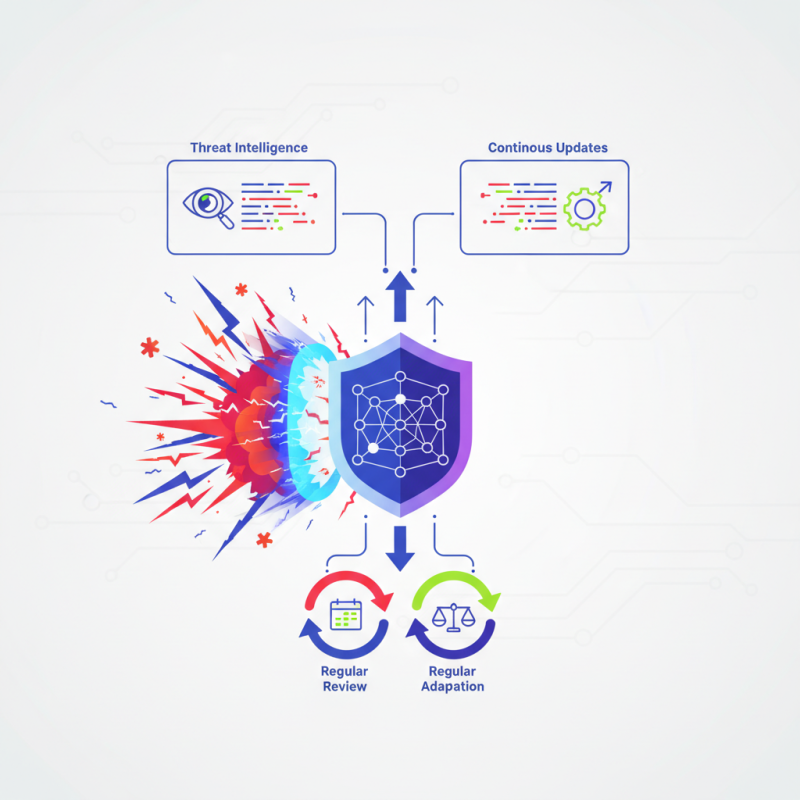
The Juniper Enterprise Firewall is designed to protect sensitive data and manage traffic securely. It operates by filtering incoming and outgoing traffic based on predetermined security rules. This ensures that only authorized users can access specific resources. This firewall can detect and block threats in real-time, which is crucial for maintaining network integrity.
Key features of the Juniper Enterprise Firewall include advanced threat detection and transparent security measures. It employs deep packet inspection to analyze data packets for malicious content. The firewall also supports high availability configurations, ensuring minimal downtime. Customizable policies allow organizations to tailor security measures based on their unique needs. Additionally, it provides detailed logs for monitoring and compliance purposes.
Despite its capabilities, there are challenges to consider. Configuring the firewall can be complex for beginners. It requires ongoing management and updates to remain effective. Organizations must invest time in training staff to use it to its full potential. Regular assessments of security policies are necessary to adapt to new threats. Continuous improvement and reflection on configurations can enhance the overall security posture.
The architecture of firewall solutions plays a crucial role in network security. Modern enterprise firewalls utilize a layered approach to protect data. Many enterprises now rely on intrusion detection systems and advanced threat prevention features. According to a recent industry report by Cybersecurity Ventures, global cybersecurity spending is expected to exceed $300 billion in 2024. This highlights the need for robust firewall solutions in safeguarding assets.
At the core of a typical firewall architecture are several components. The filtering engine examines incoming and outgoing traffic. It utilizes defined rules to determine what packets to allow or block. Some systems integrate machine learning to enhance detection capabilities. While effective, these systems can sometimes generate false positives, leading to unnecessary confusion and disruptions.
Another area to consider is deployment flexibility. Organizations can choose on-premises, cloud-based, or hybrid models. Each has its pros and cons. For instance, cloud-based systems may offer easier scalability but can also raise concerns about data privacy. A balance must be maintained between accessibility and security measures. Striking this balance isn't always straightforward and often requires ongoing adjustments to counteract evolving threats.
When considering firewall solutions, deployment models play a critical role. There are two main types: physical and virtual firewalls. Each offers unique benefits and challenges based on specific business needs.
Physical firewalls involve dedicated hardware devices. They provide robust security features and can handle high traffic loads effectively. However, hardware requires space, maintenance, and can be expensive. Some businesses may find it difficult to scale their infrastructure quickly.
On the other hand, virtual firewalls operate as software-based solutions. They can be deployed quickly in a cloud environment or on existing hardware. This flexibility is appealing, but performance can be affected by the underlying infrastructure. Latency might increase, especially under heavy loads. Choosing the right model requires careful consideration of these factors, ensuring that it aligns with evolving operational demands.
| Deployment Model | Description | Advantages | Disadvantages |
|---|---|---|---|
| Physical Firewall | A hardware appliance that provides a barrier between internal networks and external threats. | High performance, reliable hardware, and robust security features. | Higher upfront costs, limited flexibility in scaling. |
| Virtual Firewall | Firewall software that runs on virtualized environments, protecting virtual machines and applications. | Flexibility, ease of deployment, and scalability. | Potential for lower performance compared to hardware appliances, dependent on underlying infrastructure. |
The Juniper Enterprise Firewall is designed to enhance network security. One of its core functions is threat detection. This involves monitoring network activity continuously. By analyzing data, it can identify unusual behaviors that may indicate a threat. For example, if a sudden spike in data consumption occurs, this could be a sign of a security breach. Real-time alerts notify administrators immediately, enabling swift responses.
Prevention mechanisms are equally vital. The firewall implements various methods to block potential threats. This may include filtering out malicious traffic before it reaches sensitive areas. It inspects incoming and outgoing packets. Intrusion Prevention Systems (IPS) are also part of this arsenal. They actively disrupt attacks by closing off compromised sessions.
However, there are limitations. No system is infallible. Sometimes, legitimate traffic might get filtered out, causing disruptions. Constant tuning and monitoring are required. Balancing security and accessibility is a challenge that demands ongoing attention.
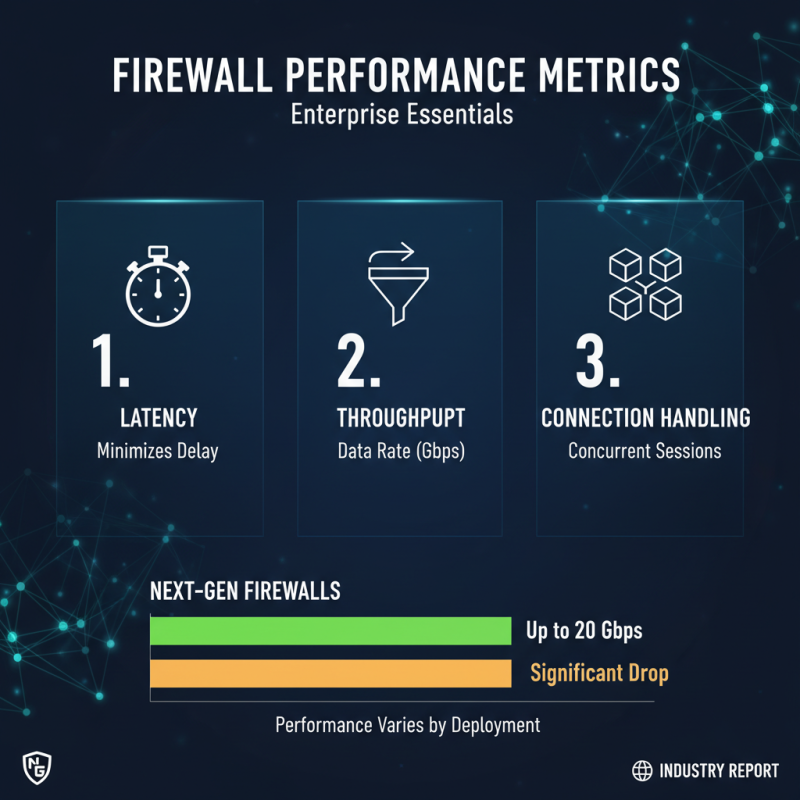
When evaluating firewall performance, metrics are crucial. In enterprise environments, latency, throughput, and connection handling determine a firewall’s effectiveness. According to the last industry report, performance can vary based on deployment settings. For instance, next-gen firewalls maintain a throughput of up to 20 Gbps. Yet, actual performance can drop significantly under heavy loads.
Another vital metric is the concurrent connections handled. Leading firewalls can support millions of connections. However, real-world scenarios often show that some products struggle with complex traffic. An analysis indicated that around 30% of enterprises experience performance degradation during peak times. This discrepancy highlights the need for continuous monitoring and testing.
Organizations must also consider resource usage. Firewalls require CPU and memory to function optimally. Data suggests that firewalls may use up to 70% of available hardware resources in demanding applications. Such info calls for careful evaluation and potential adjustments. Ignoring these aspects can lead to vulnerabilities that hackers might exploit. Hence, periodic assessments of these metrics are essential for maintaining security and performance.








